In This Post
Explore the rise of malvertising in September. Learn about the latest tactics in malicious online ads and how to protect yourself.
September is a month of changeâsummer holidays come to an end, school kicks off and cybercriminals engage in increases illicit online activities.” According to our data, the month of September commonly sees a sizable increase in the number of cyber threat detections reported across multiple vectors when compared to preceding summer months. Notably, within September we observed two particularly pronounced surges in the volume of malicious advertising incidents, also known as “malvertising”.
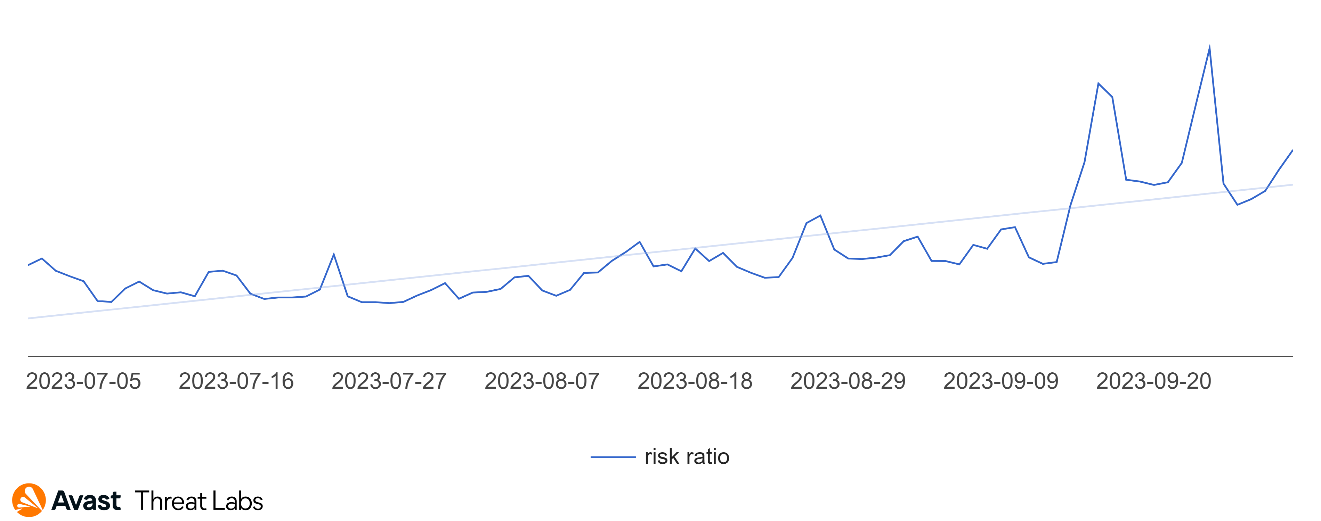
This September rise in detected cyber threats is likely a consequence of shifting behaviors as individuals resume regular work and school schedules following the more relaxed pace typical of the summer holiday period. Cybercriminals may take advantage of this transition, operating under the assumption that heightened online activity and connectivity provides additional opportunities to widely disseminate malware or steal personal information.
What is Malvertising?
Malvertising is a malicious online advertising technique that involves the distribution of malware through online ads or, in some cases, in conjunction with browser push notifications. Cybercriminals use these seemingly legitimate ads to deliver malware to unsuspecting users’ devices when they click on or interact with the compromised advertisements.
Cybercriminals are smart enough to make their malvertising pop-ups look genuine. Frequently, these fraudulent pop-ups exploit the recognizable antivirus companys logo. The goal is to convince users they are encountering a legitimate notification from an antivirus provider. These alerts typically display messages that a virus on a computer has been found and that the subscription plan has expired.
Upon clicking these deceptive pop-ups, unsuspecting users may find themselves redirected to a fake website. These fraudulent sites often take the form of straightforward phishing pages, where users are asked to enter personal credit card information under the guise of providing antivirus services. The scam can take many forms.
We have warned about malicious push notifications in previous reports; this quarter is no exception. This method continues to remain popular with scammers as its effectiveness is still considerable, especially on mobile phones.
Malvertising is a portmanteau of “malicious software (malware) advertising” 1. It is the use of online advertising to spread malware and other threats. Malvertising involves injecting malicious or malware-laden advertisements into legitimate online advertising networks and webpages 12. It can be hard to detect and prevent, as it can silently work its way into a webpage or ad without user action 3. Malvertising uses what looks like legitimate online advertising to distribute malware and other threats with little to no user interaction required 3. Malvertising can appear on any advertisement on any site, even the ones you visit as part of your everyday Internet browsing 3. Malvertising criminals rely on two main methods to infect your computer. The first is an advertisement that presents some kind of provocative enticement to get you to click on it. The lure might come in the form of an “alert,” such as a warning that you already suffer from a malware infection. Or it might be an offer for a free program. Such tactics use social engineering to scare or tempt you into clicking on a link. Give into that temptation and you are infected. Even more nefarious is the second method, known as a drive-by download. In this case, the infected ad uses an invisible web page element to do its work. You don’t even need to click on the ad to trigger the malicious activity. Just loading the web page hosting the ad (or a spam email or malicious pop-up window) redirects you to an exploit landing page, which takes advantage of any vulnerabilities in your browser or holes in your software security to access your machine 3. To protect yourself from malvertising, it is recommended to use an ad-blocker, keep your software up-to-date, and use a reputable antivirus program 314.
Types of Malvertising
Malvertising comes in a few different types. Here are two of the main ones weve seen this quarter.
One of the most common examples of this malvertising was a page that fell into the push notification section that often appeared as part of a redirect chain. This page has multiple variations. The main purpose is to simply convince the user to allow push notifications.
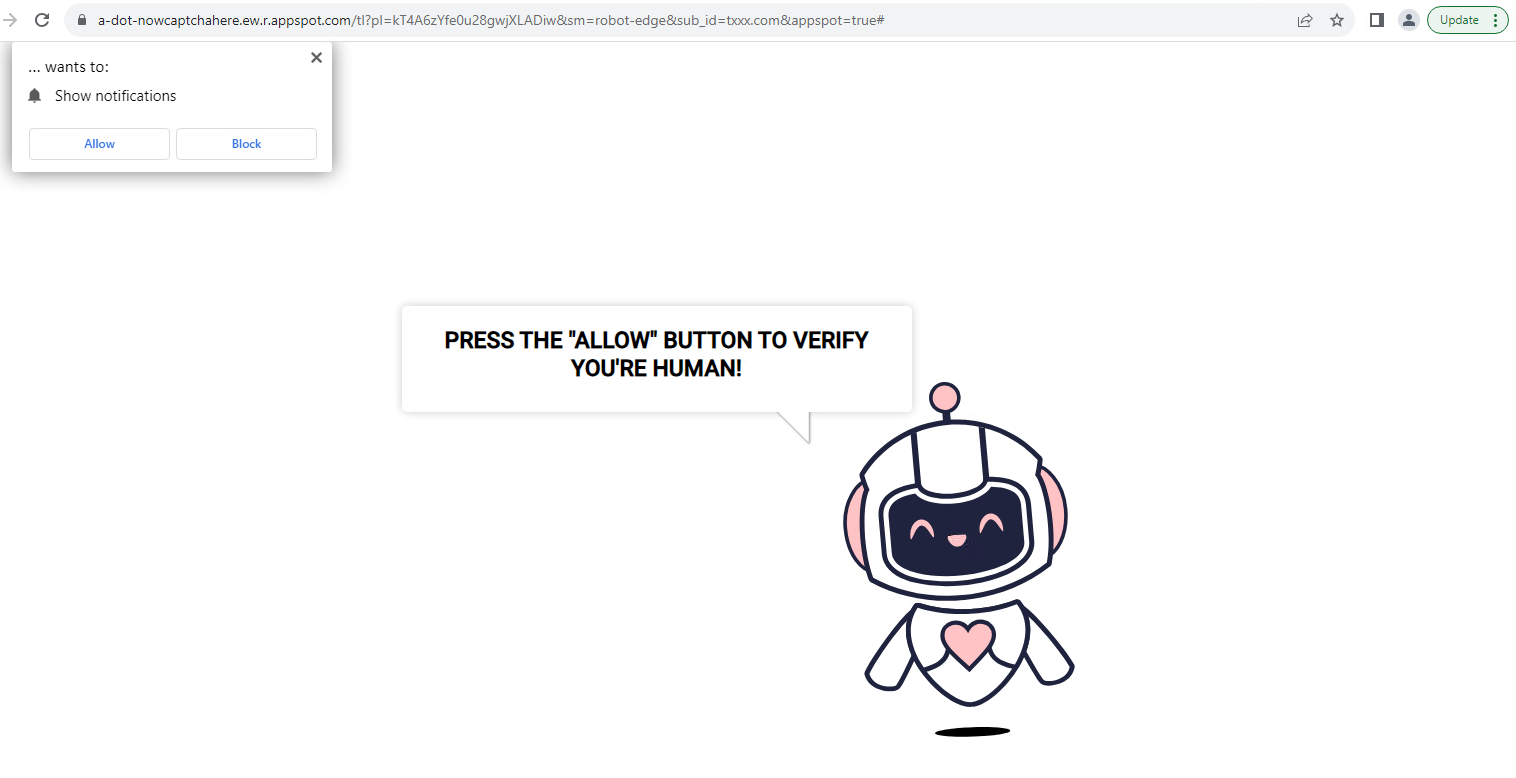
Push notifications can be especially effective on mobile devices, where they can also be disguised as system notifications, such as an unanswered call or a new text message.
Push notifications are not the only powerful tool for scammers. We have reported many times that scammers like to use advertising space on popular social networks. This way of promotion is especially dangerous because many users consider their social platforms to be a safe and personal space. Scammers also design their ads to attract attention, often by using catchy text or the faces of famous personalities. Thanks to this, the success rate of these campaigns is quite high.
Another big advantage for scammers utilizing social media ads is their ability to precisely target and tailor content to vulnerable users. Consequently, users may find their social media feeds full of these types of ads over time. In the example below, the malvertiser uses the Tesla and Elon Musk names to hook people.
These above ad examples are from Facebook. In this case, these ads are part of a single fraudulent financial scam where scammers are trying to trick users into investing in an Elon Musk/Tesla project. After clicking on the ad, the user is redirected to a web page where they are informed about the great benefits and the certainty that this project is profitable. In neither case were the ads created by the subject names (Elon Musk or Tesla).
As above, this example of malvertising uses a name brand (Tesla) to give the impression of professionalism. Part of the scam is also an appeal to the unrealistic possibility of buying through an ‘automatic robot’ that invests itself and ‘automatically’ earns money.
These fake sites can take many forms. Often there are variations that mimic the world’s famous media such as BBC News and many others. These ads take advantage of the targeting of ads that social platforms allow them to do; the ads click through to websites that are created for users in individual countries that correspond to popular news sites in those countries.
The landing pages in this campaign also contain a registration form that requires users to enter their contact information. This information is then sent to the scammer, who then contacts the user either by email or, more often, by phone. Then the actual scamming effort is done over the phone.
After filling out these fraudulent forms, the user can expect a phone call from the fraudsters. The caller subjects the prospective buyer to a thorough questioning, giving the impression that the financial company is checking not only the solvency of the prospective buyer but also their professional and financial knowledge level. The prospective client is then persuaded to install a remote computer access application, in this case, usually AnyDesk.
According to a report by Clean.io, Facebook’s embedded browser was the biggest source of malvertising threats in 2020, accounting for 52.4% of all attacks by volume 1. The total cost of cybercrime (including malvertising attacks) worldwide went from $3 trillion per year in 2015 to over $6 trillion in 2021 1. Malvertising attacks have increased by over 70% during the COVID-19 pandemic peaks 1. The damage of malvertising and other malware-related frauds is estimated to reach $10.5 trillion by the end of 2025 1.
How to avoid falling for a malvertising scam
- do not disclose your personal information to people you do not know or cannot authenticate
- do not send photocopied personal documents
- do not send any printed credit card information
- do not give a code that would allow someone to access your computer remotely
- if someone is remotely connected to your computer for any reason, do not log into your online banking
- do not forward or tell anyone SMS bank authorization codes
- do not authorize a payment to a stranger
- keep an antivirus program installed on your computer
- keep your online banking limits as low as possible and increase them only to the actual need to pay a specific payment
Note: Real samples found on the web, not generated by us. Any logos or trademarks displayed are the registered trademarks of their respective brands.
Source: AVAST SECURITY AVAST rise of malvertising latest tactics in malicious online ads protect yourself Facebook

